As highlighted in the 2014 IOCTA, the rise of the Internet of Things (IoT) or the Internet of Everything (IoE) is seen as a major challenge for law enforcement together with Big Data and the Cloud. Being able to keep up with the pace of technological development will require law enforcement to constantly update their digital forensics capabilities.
Based on the feedback received, Big Data for law enforcement usually means a lot of data which is often referred to as the volume challenge. Cases involving several terabytes of data for one suspect are becoming more common, which has a considerable impact on investigations in terms of resources and time, making it more difficult for law enforcement to find the proverbial needle in the haystack. For instance, in one of the cases the amount of data exceeded 100 terabytes. This has stimulated research into tools and methods to improve the handling and analysis of large quantities of data1.
While the potential benefit of Big Data for more efficient, proactive and preventive police work is generally accepted2, specifically in relation to predictive policing, it appears that the majority of EU law enforcement agencies are not at a stage where Big Data analytics is being used to its full potential or even considered at all. The potential benefits identified by law enforcement include improved and more targeted analytical capabilities, an increased chance to find relevant evidence, better support for the triage process and the ability to create a denser timeline of events, and the support for the automated analysis of crime-relevant data, including speech and video recognition.
While the IoT is still seen as an emerging threat from a law enforcement point of view3, the rising number of smart ‘things’, including smart homes, smart cars4 5, smart medical devices6 and even smart weapons7 are a clear indicator of its growing adoption8. This contributes to an increasing digitisation and online presence of personal and social lives, and an increasing level of interconnectivity and automation, which creates a number of challenges in terms of privacy, security, and trust. Law enforcement needs to be prepared to address the criminal abuse of such devices and of the data that is generated or collected via the IoT.
The Cloud is an enabler for IoE and Big Data by providing the distributed and scalable resources needed to handle the data growth and provide the necessary processing services. Data together with entire infrastructures will continue to move to the Cloud, which is already creating technical and legal challenges for law enforcement. Equally, criminals aim to abuse Cloud services such as popular file synchronisation services9, for instance to host malware or C&C structures, as they are less likely to see any traffic blocked by security systems.
For law enforcement, the top challenges in relation to smart devices and the Cloud are:
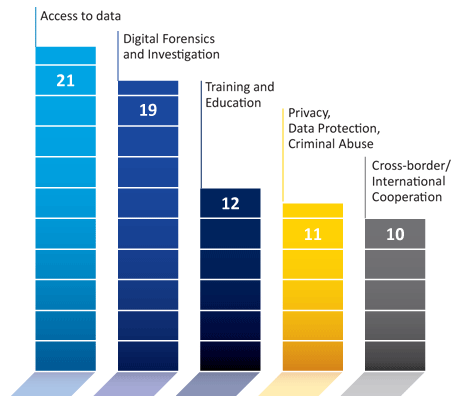
Of the questionnaire responses received from EU law enforcement, three agencies indicated that they were organising or were planning on organising training programmes on the IoT and the Cloud. Three agencies specified that they were cooperating with private industry on this topic. One law enforcement agency supported preventive activities in this area.
However, the feedback provided by law enforcement also identifies several opportunities with regard to the IoT and the Cloud: