It is increasingly clear that any internet facing entity, regardless of its purpose or business, must consider itself and its resources to be a target for cybercriminals. When taking into account the safety and security of these networks, there are a number of key threats that must be considered.
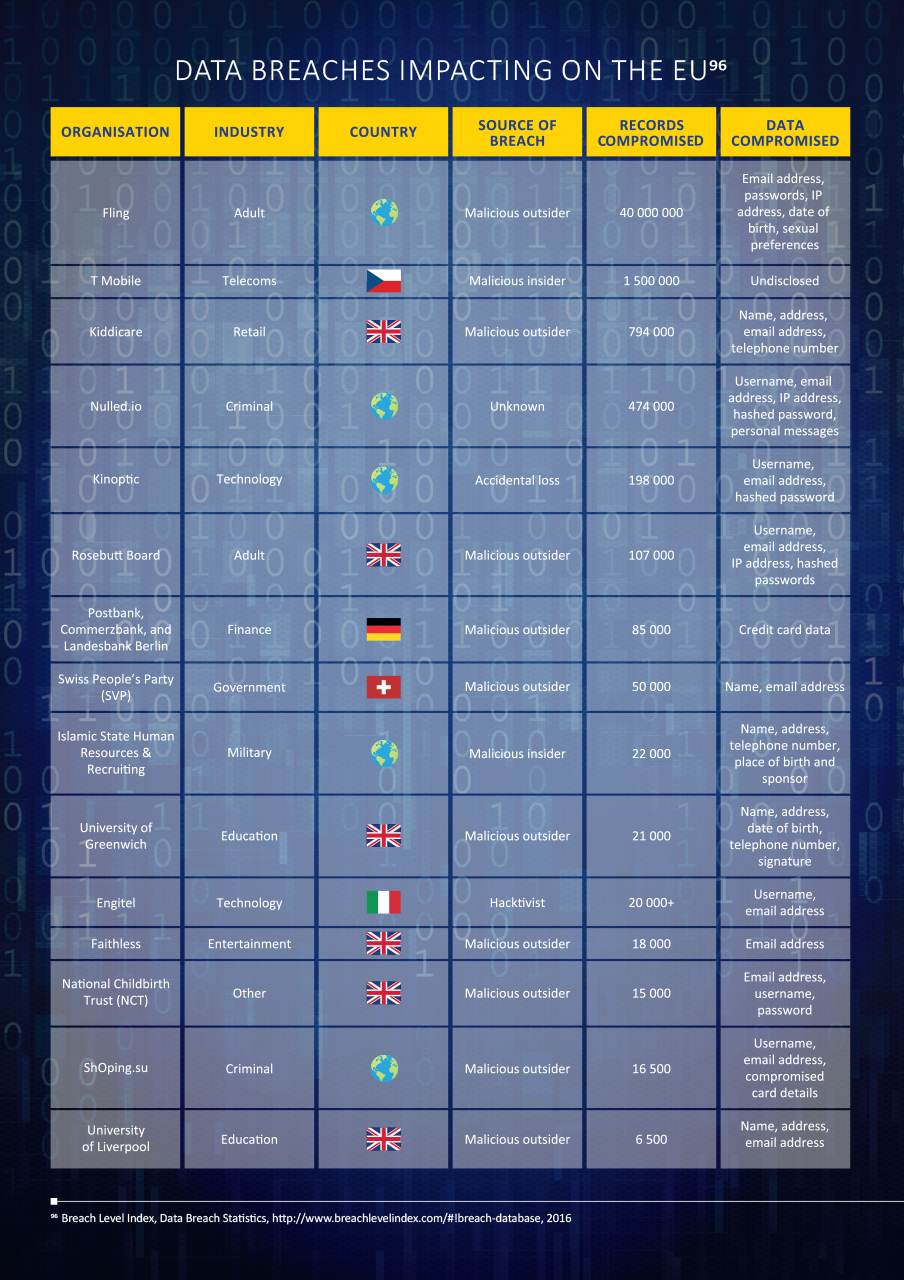
The following table outlines some of the data breaches from the first half of 2016 that impact on the EU. These breaches originate either from within the EU, or from outside the EU, but involve significant numbers of EU citizens. In this context, a breach is defined as an incident that results in the confirmed disclosure (not just potential exposure) of data to an unauthorised party95.

Among the wide range of services offered in the digital underground, DDoS is one of the most popular. This particular type of attack can be used by cybercriminals, not only launch to attacks on public and private organisations and businesses, but also on their own competitors and rivals75,76.
In our last report it was indicated that attacks over 100 Gbps77 were uncommon. Later in 2015 there were reports of attacks exceeding 300 Gbps. 2016 has already seen record attacks allegedly exceeding 600 Gbps, targeting the global website of the BBC and US presidential candidate Donald Trump’s website78. These attacks were intended to demonstrate the effectiveness of a new DDoS-as-a-service tool BangStresser. Indeed, tools such as these, commonly referred to as ‘booters’ or ‘stressers’ and readily available as-a-service on the internet, accounted for a significant proportion of DDoS attacks reported to law enforcement.
Half of EU Member States reported investigations into DDoS attacks. While a significant proportion of these attacks were attempts at extortion, these attacks were often either purely malicious or had an unclear motive.
Throughout 2015 two names dominated the DDoS attack scene – DD4BC (DDoS for Bitcoin) and the Armada Collective, receiving wide coverage in the media.
In December 2015, law enforcement agencies from Austria, Bosnia and Herzegovina, Germany and the United Kingdom joined forces with Europol and the J-CAT for Operation DD4BC, targeting the cybercriminal group DD4BC. The operation resulted in the arrest of a main target and resulted in the cessation of attacks from both DD4BC and the Armada Collective.79
The Armada Collective was suspected to be a copy-cat, as their tactics bore many similarities and both stopped their activities following the arrests in December 2015. Both groups have spawned scammers who continue to extort enterprises based on the reputation of the original criminal gangs, demanding ransoms or ‘protection money’ when they in fact lack both the intention and capability to launch such an attack80.

Almost half of Member States indicated that they had been involved in investigating attacks on private networks. The primary criminal intent for these attacks was to steal data, although there were additionally half as many attacks that related to VoIP81 fraud or were simply malicious. Over a third of Member States also reported investigations into attempts specifically to gain unlawful access to intellectual property. Both industry82 and law enforcement see similar patterns in the techniques used to obtain such unauthorised access, with hacking and exploiting network vulnerabilities as the most common technique, followed by malware and then social engineering. It has been suggested that Dridex, one of the key malware threats identified in this year’s report, was likely a major factor in these attacks83.
While there are no specifics from law enforcement, other reporting indicates that industries such as accommodation and retail account for a significant percentage of breaches as the data from these sources are highly valued by financially motivated criminals84. Virtual currency exchangers, as well as traders on these platforms are particularly attractive targets for hacking attacks. 2016 has seen a number of exchanges being successfully hacked with both company and customer funds directly transferred to the attackers, via pseudonymous payment mechanisms (usually Bitcoin) which prevents retrieval of the funds. Some reports indicate that up to 89% of data breaches have a financial or espionage motive85.
It is not only financial credentials or intellectual property that is desirable however. 2015 saw the healthcare industry heavily targeted by attackers86,87. Moreover, following the breaches of Ashley Madison and AdultFriendFinder earlier in 2015, there appears to be a trend in targeting online services catering to ‘consenting adults’, with further breaches occurring in 2016. Criminals targeting these services can gain not only financial data for using in financial fraud, but also potentially compromising sensitive customer data which can additionally be used for extortion88.
Cryptsy, Shapeshift, Gatecoin and Bitfinex all suffered large scale hacks in 2016. The Bitfinex breach in particular, resulting in loss of almost 120,000 bitcoins89 represents the largest loss of funds since the notoriously known Mt. Gox incident in early 2014 when over 744,000 bitcoins was lost. Unlike most attacks in early years of the technology, many companies affected by recent criminal activity have reported the incidents to law enforcement and actively support investigation efforts.
Interestingly, a number of services in the criminal underground were also breached9091, disclosing credentials and other attributable data used by cybercriminals during their online activity. The identity of the perpetrators of these attacks is unknown, but whether coming from a ‘white hat’, rival criminal or cyber-vigilante, such disclosures provide law enforcement with a wealth of invaluable information.
Private Branch Exchange (PBX) or Dial Through fraud is by no means a new crime, having been around for more than 20 years, however the shift to IP-based networks has created new opportunities for criminals. PBXs are telephone systems used by businesses to communicate both internally and externally. PBX fraud is the routing of calls to premium rate or special service numbers through a compromised exchange. Attackers running these premium phone lines can make significant profits92, while the hacked company is liable for the call charges, which can escalate rapidly. Unlike other types of network attacks, PBX fraud seldom makes the news despite being one of the biggest financial threats facing businesses operating in the VoIP space, or any business operating an IP-enabled PBX93. Globally, PBX fraud costs industry in excess of €34 billion per year94.
Over one quarter of Member States reported investigations into this type of fraud, with those that did so almost unanimously agreeing that the threat is growing.

While probably representing the least sophisticated type of attack in this category, the defacement of public and private websites belonging to government and industry is nonetheless a common one. Over one third of Member States and many non-EU states investigated website defacements. Often, case numbers were low, however such incidents were especially widespread following terrorist attacks. Consequently, France and Belgium were particularly affected in 2015/2016. Hacktivism appears to be the primary motivation behind the majority of these attacks, although a significant number were purely malicious.

If current trends continue, it is obvious that DDoS attacks will continue to grow in scale, with the current top-end attacks becoming the norm as attacks reach new heights in terms of bandwidth and volume. While security providers must continue to match the scale of these attacks with mitigation solutions, the primary response for law enforcement remains unchanged – the arrest of perpetrators. Such a response does however require the timely involvement and competent action of the appropriate authorities.
The growing Internet of Things will expand the range of (often insecure) internet connected devices potentially capable of participating in DDoS attacks97. Coupled with IPv6, providing unlimited unique IP addresses and likely a host of undiscovered vulnerabilities, it is fertile ground for botnets98.
Data will always be a key commodity for cybercriminals but the ways that cybercriminals use or interact with it will continue to evolve as different data types are targeted for new purposes. Data is no longer just stolen for immediate financial gain, but can be used for the furtherance of more complex fraud, encrypted for ransom, or used to disrupt rivals or directly for extortion. Alternatively, when considering the illegal acquisition of intellectual property it can represent the loss of years of research and huge investment by the victim. It can be expected that while the compromise of financial data will continue, other sensitive data sources will increasingly be targeted such as the healthcare sector.
In areas where data plays a key role, such as the pharmaceutical sector which has sometimes decade-long research, testing and approval cycles to develop drugs that support precision personalised medicine, targeted attacks to exfiltrate such data sets are likely to increase.


 Click here to open this table
Click here to open this table