

Cyber-dependent crimes are offences that can only be committed using a computer, computer networks or other form of information communications technology. Cybercrime is a global phenomenon affecting all Member States and is as borderless as the internet itself. The attack surface continues to grow as society becomes increasingly digitised, with more citizens, businesses, public services and devices connecting to the internet.
OPERATION AVALANCHE 15
On 30 November 2016, after more than four years of investigation, the Public Prosecutor’s Office Verden and the Lüneburg Police (Germany) in close cooperation with the United States Attorney’s Office for the Western District of Pennsylvania, the Department of Justice and the FBI, Europol, Eurojust and global partners, dismantled an international criminal infrastructure platform known as ‘Avalanche’. The Avalanche network was used as a delivery platform to launch and manage mass global malware attacks and money mule recruiting campaigns. The monetary losses associated with malware attacks conducted over the Avalanche network are estimated to be in the hundreds of millions of euros worldwide, although exact calculations are difficult due to the high number of malware families managed through the platform. The global effort to take down this network involved the crucial support of prosecutors and investigators from 30 countries. The operation marks the largest-ever use of sinkholing to combat botnet infrastructures and is unprecedented in its scale, with over 800,000 domains seized, sinkholed or blocked.
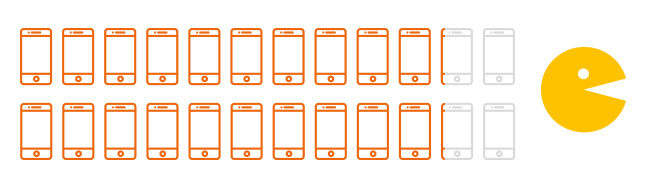
85%
of internet users feel at risk of becoming a victim of cybercrime
The CaaS model provides easy access to tools and services across the entire spectrum of cyber-criminality, from entry-level to top-tier players, including those with other motivations such as hacktivists or even terrorists. This allows even entry-level cybercriminals to carry out attacks of a scale disproportionate to their technical capability. Criminal forums and marketplaces within the deep web or Darknet remain a crucial environment for cybercriminals to communicate and are a key component for CaaS.

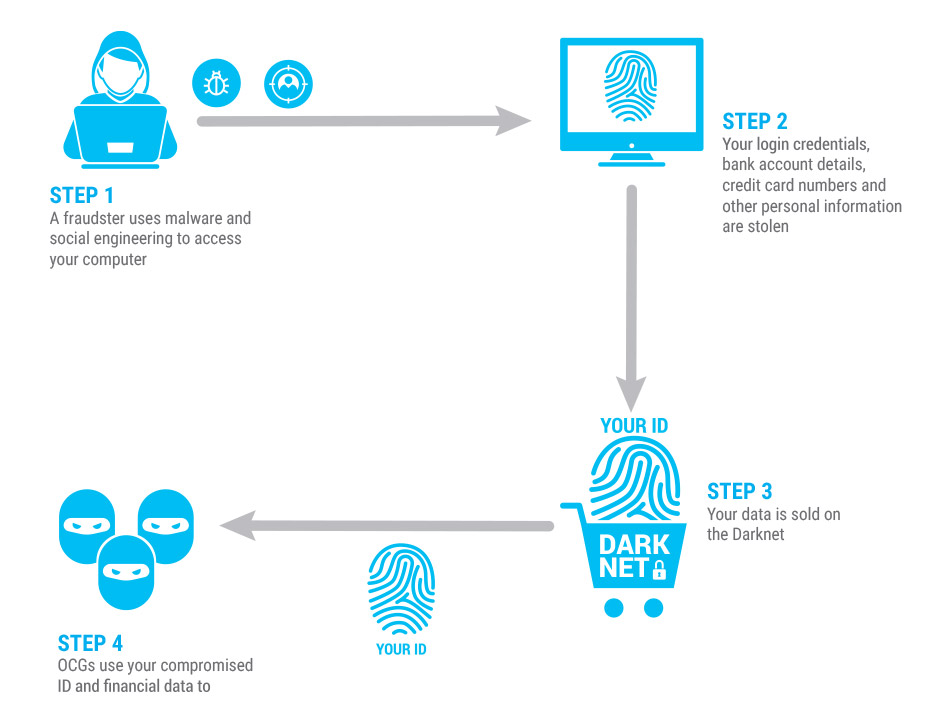
Malware typically steals user data such as credit card numbers, login credentials and personal information from infected machines for subsequent use by criminals in fraud.
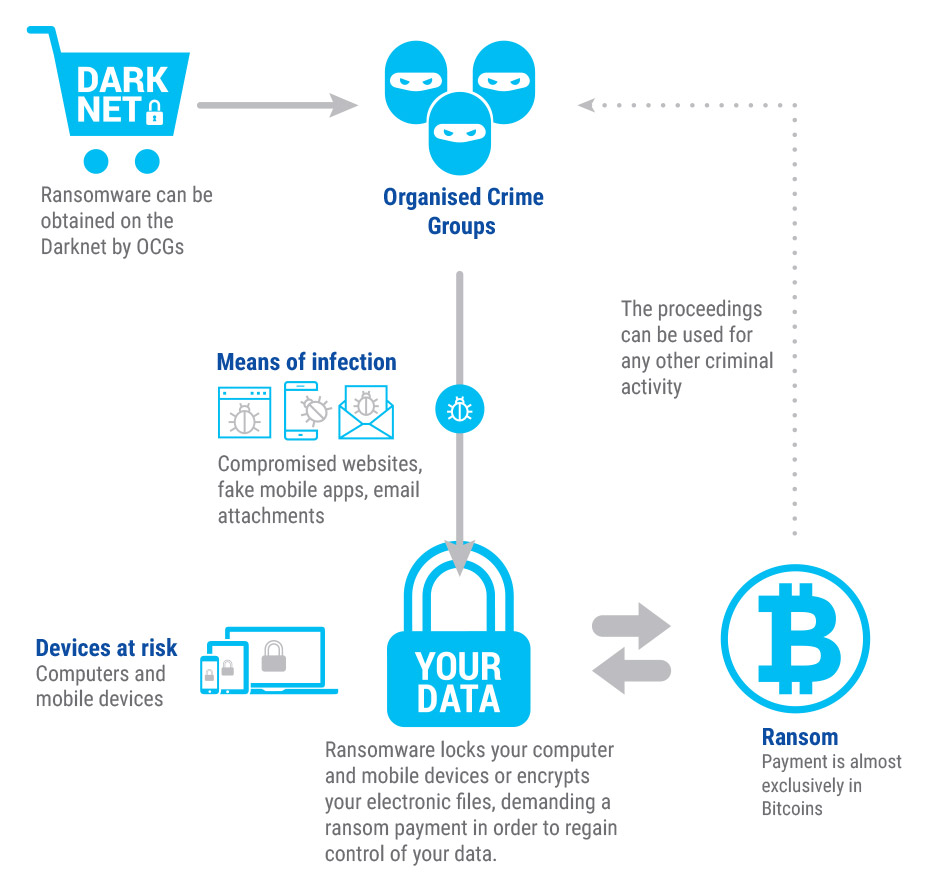
Cryptoware (ransomware using encryption) has become the leading malware in terms of threat and impact. It encrypts victims’ user generated files, denying them access unless the victim pays a fee to have their files decrypted.

Network intrusions that result in unlawful access to or disclosure of private data (data breaches) or intellectual property are growing in frequency and scale, with hundreds of millions of records compromised globally each year.

Criminals use fraudulent transfer orders to defraud private and public sector organisations. Fraudsters heavily rely on social engineering techniques and malware to carry out this type of fraud.

Compromised card data is readily available and easy to obtain on forums, marketplaces and automated card shops in the deep web and Darknet.

Child Sexual Exploitation Material is increasingly produced for financial gain and distributed through the Darknet. Coercion and sexual extortion are increasingly being used to victimise children.
The development and distribution of malware continues to be the cornerstone for the majority of cybercrime. Informationstealing malware, such as banking Trojans, still represent a significant threat. This type of malware typically steals user data such as credit card numbers and login credentials from infected machines for subsequent use by criminals in fraud.
Since late 2013, cryptoware (ransomware using encryption) has become the leading malware in terms of threat and impact. Cryptoware encrypts victims’ user generated files, denying them access unless the victim pays a fee to have their files decrypted. Following the trend of information stealers, cryptoware campaigns are increasingly targeting public and private sector entities.
Network attacks vary in modi operandi and purpose. Website defacement is a common but low-impact attack, and often the trademark of hacktivist groups targeting government or public websites.
Network intrusions that result in unlawful access to or disclosure of private data (data breaches) or intellectual property are growing in frequency and scale, with hundreds of millions of records compromised globally each year. 16 Compromised data can be used for a variety of criminal purposes including fraud and extortion 17 and is highly valued by financially motivated criminals. 18
Some Member States highlight the particular threat posed by insiders to a company’s security. Any sector or network which holds data which can be monetised is a target for such attacks.
Data has become a key commodity for criminals.
Increasing internet connectivity by citizens, businesses and the public sector, along with the exponentially growing number of connected devices and sensors as part of the Internet of Things will create new opportunities for cybercriminals. Malware targeting smart devices will lead to new sources of data leakage and network compromise and create new botnets. Given the ease of entry into cybercrime, the use of cyber tools and services by traditional OCGs to enhance or expand their capabilities is likely to become more commonplace.

While neither offline nor online CSE meet the criteria to be considered ‘organised crime’ this is still a high priority crime due to the degree of physical and psychological damage to one of society’s most vulnerable groups – children.
Online and offline child sexual exploitation are often considered two different crime areas. However, a number of offenders are involved in both. There are indications that this is the case for about 30% of offenders in possession of CSEM.
The increasing global availability of broadband internet and internet-enabled devices continues to fuel the growing number of both offenders and victims in this area. While the same can be said of any number of crime areas, this phenomenon is a major contributor to online CSE.
The internet provides offenders and potential offenders with an environment in which they can operate with an enhanced level of safety and anonymity. In particular, there is a growing number of forums on the Darknet dedicated specifically to the production, sharing and distribution of CSEM. Typically this refers to services on the TOR network. Peer-to-peer (P2P) file sharing applications are the preferred method of exchanging CSEM.
Children are sexually exploited largely to satisfy the sexual appetites of those with a sexual interest in children. However, there is a growing trend in the production of CSEM for financial gain. A particular activity associated with commercial production of CSEM is that of Live Distant Child Abuse (LDCA). LDCA is a significant threat in this area of criminality. LDCA involves a perpetrator paying to direct the live abuse of children on a pre-arranged specific timeframe through video sharing platforms.
There is a growing trend in the production of Self-Generated Indecent Material (SGIM) - typically teens or pre-teens taking indecent images of themselves to be shared privately with a partner or someone they believe they can trust, for example in grooming scenarios. Subsequently, these images can be distributed either accidentally or maliciously without the owner’s consent.
Often associated with the production of SGIM is the growing practice of sexual extortion, whereby an offender uses an explicit image of a minor - obtained incidentally or through coercion or deception - to further coerce or extort the child into either producing more material or engaging in further online or even offline abuse. In some cases the perpetrator alternatively seeks financial gain. 19

Payment card fraud is a low-risk, high-profit activity. Compromised card data is readily available and easy to obtain on forums, marketplaces and automated card shops in the deep web and Darknet. Payment card fraud can be split into two distinct crime areas: Card-present fraud and card-notpresent fraud.
CP fraud requires an offender to present a physical card at an automated teller machine (ATM), Point of Sale (POS) or other terminal. This crime has two stages: obtaining a card, and the use of the card. The cards used are either lost or stolen genuine cards, or counterfeit cards. Unlike fraud using lost or stolen cards, fraud using counterfeit cards is typically committed outside the Single Euro Payments Area (SEPA).
Some OCGs have partly industrialised their processes, using workshops to produce counterfeit cards.
CNP fraud involves the use of card data to make fraudulent purchases online or by telephone. Unlike CP fraud, the data required is only that needed to make an online credit card purchase – the name of the card holder, billing address, card number, expiry date and security code. The fraud, commonly referred to as ‘carding’, is committed across all sectors but the purchase of physical goods, airline tickets, car rentals and accommodation with compromised cards have generally seen an increase throughout the EU. Where CNP is used to fraudulently purchase goods, like CP fraud, offenders will typically purchase high-value goods with the intention of reselling them. Offenders will often use packet mules or reshipping services to safely receive their fraudulently obtained goods.
CNP is fuelled by the availability of compromised card data resulting from data breaches, information stealing malware and phishing. As many data breaches often involve the compromise of millions of card details at once, there is a considerable excess of card data compared to the demand. Among the places where compromised card data can be found are an increasing number of illegal carding sites on both the deep web and Darknet where not only card data can be purchased but offenders can learn about how and where to ‘card’. New payments methods provide offenders with new opportunities to use compromised card data. By uploading the card data to smartphone services, offenders can make “in app” or “on site” payments to apps which they control.
The growing e-commerce industry will result in a parallel growth of CNP fraud, especially as industry measures at preventing CP fraud become more effective. Criminal modus operandi will be shaped by industry measures to counter payment card fraud.
Emerging and alternate payment options such as contactless payment using Near Field Communication (NFC) will drive innovation within OCGs to enable them to abuse new technologies. New electronic/ card-less payment methods may however ultimately result in a downwards trend in card fraud.
INTERNATIONAL CRIMINAL NETWORK BEHIND LARGE-SCALE PAYMENT FRAUD DISMANTLED 20
In September 2016, Italian and Romanian law enforcement authorities supported by Europol disrupted an international criminal group responsible for large-scale misuse of compromised payment card data, prostitution and money laundering. The criminal network used sophisticated ATM skimming devices which allowed them to compromise ATMs and deceptive phishing techniques to perform a high volume of fraudulent transactions. Estimated losses incurred by the criminals’ activities amount to several hundred thousands of euros. Micro-camera bars, card readers, magnetic strip readers and writers, computers, phones and flash drives, several vehicles, as well as thousands of plastic cards ready to be encoded were seized in several locations.
GLOBAL ACTION AGAINST AIRLINE FRAUDSTERS 21
Global Airport Action Days combine the efforts of law enforcement and private sector partners to combat the fraudulent online purchases of flight tickets, which is estimated to cost the industry over EUR 1 billion per year. Fraudulent online transactions are highly lucrative for organised crime and are often purchased to facilitate more serious criminal activities including migrant smuggling, THB, drug trafficking and terrorism. In October 2016, the fifth Global Airport Action Day was organised through coordination centres at Europol, INTERPOL Global Complex for Innovation in Singapore and Ameripol in Bogota. The activity was supported by Canadian and US law enforcement agencies. Representatives from airlines, online travel agencies, payment card companies, Perseuss and the International Air Transport Association (IATA) worked together with law enforcement officers deployed in the airports. Eurojust assisted throughout the action week, together with the European Border and Coast Guard Agency (Frontex) which deployed officers to 20 airports, assisting in the detection of identity fraud, fake documents and migrant smuggling. 193 individuals suspected of traveling with airline tickets bought using stolen, compromised or fake credit card details were detained. 43 countries, 75 airlines and 8 online travel agencies were involved in this global operation which took place at 189 airports across the world.
