Chapter 3 - Crime Areas
3.7 Data breaches and network intrusions - Overview
Any sector will hold data of value or interest to another entity, whether that entity is a financially or politically motivated cybercriminal, a competitor or foreign state. Furthermore almost any type data has worth, from card data to medical records to intellectual property. As a consequence all sectors are affected by data breaches and network intrusions [112]. Although the motivation for most data thefts is largely financial gain, the proportion of attacks for the purpose of espionage is steadily increasing [113]. Not every attack revolves around data theft however; attacks can also be for the purpose of extortion, protest (hacktivism) or sabotage.
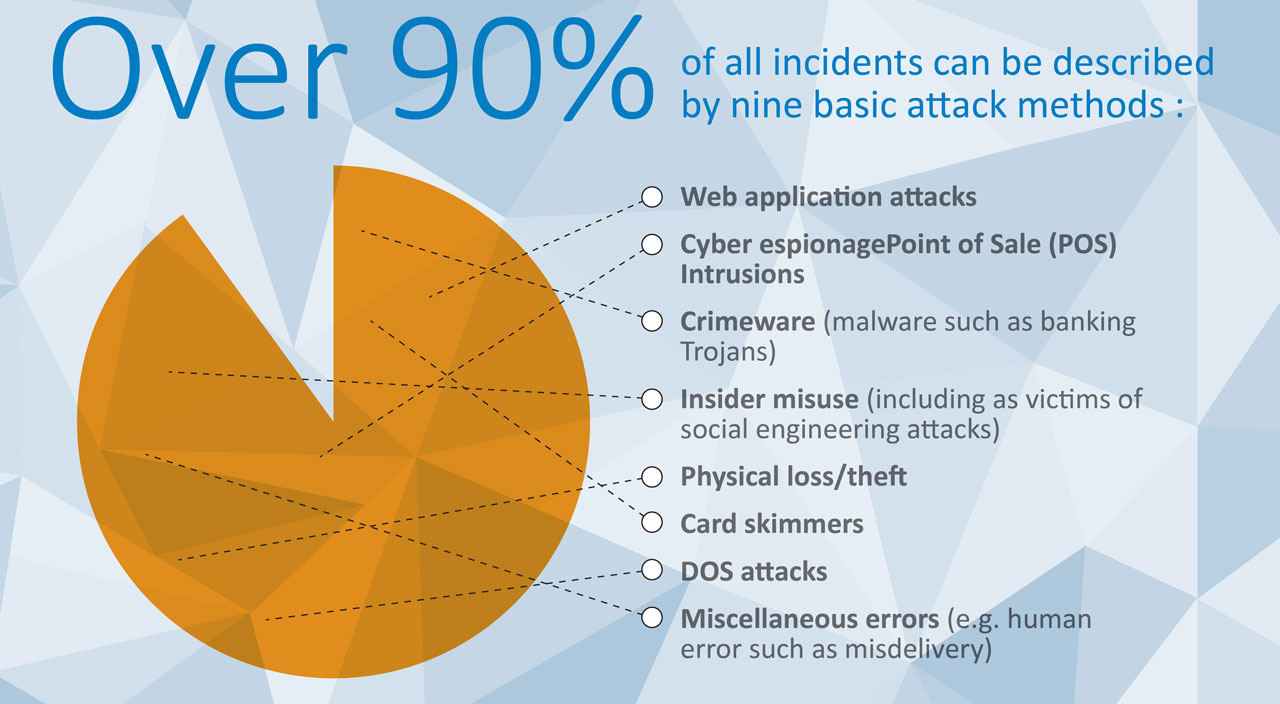
(Source [114])
In 2013 web application attacks, cyber espionage and POS intrusions accounted for over 70% of all breaches - a breach being defined as an incident where data either was, or was potentially, lost. The costs of a breach are estimated to be up to USD 200 per record, with malicious attacks being the most costly [115].
Of all the sectors seeing victims of data breaches, the financial sector was most heavily hit, followed by the public sector, retail, the accommodation sector and utilities. Those sectors which are heavily regulated (healthcare, education, financial, etc.) also have the highest costs per capita from a breach [116].
The scale of these breaches can be immense. In December 2013, an attack on US retail company Target resulted in the exfiltration of details of up to 70 million customers and 40 million credit cards. In February 2014 a breach at eBay resulted in the disclosure of 145 million customer details as a result of a hacking attack [117]. The data lost included customer names, email addresses, physical addresses and phone numbers. The breach represented one of the largest breaches to date.
Many intrusions are executed as what is termed an Advanced Persistent Threat (APT). These are multi-stage attacks which take place over an extended period. In 2013 the average period of time an attacker remained undetected on a compromise network was 229 days [118]. Such attacks typically begin with the attacker attempting to identify vulnerable entry points. The actual incursion will generally use one or a combination of methods from social engineering, malware attacks and hacking. Once ‘inside’ the attackers will map the compromised network, deploy additional malware to facilitate further access and capture information and valuable data. The final stage is to exfiltrate the captured data to be used for whichever criminal purposes it can be exploited.
Once exfiltration occurs the likelihood of discovery significantly increases although as little as one third of compromises are discovered by the target company themselves [119] with many disclosures being discovered by LE or third party threat researchers [120].
The increasing proportion of these attacks which relate to some form of hacking or malware can be attributed to the increasing availability of crimeware kits and hacking services available on the digital underground [121] and the extent to which attacks can now be automated. Social engineering techniques typically consist of spear phishing or watering hole attacks [122], [123].

In 2013 over 50% of attacks targeted the USA. Almost half of these attacks nominally originate from Eastern Asia, with a further fifth originating from Eastern Europe. State-affiliated attacks are believed to account for almost 90% of all attacks, while organised crime is believed to be responsible for just over 10% [124].
EU Member States investigated a number of data breaches and network intrusions. Notably there were a number of attacks on critical infrastructure - with telecommunications companies being a common target. Other instances involved breaches into private industry and government sectors and were primarily motivated by financial gain, although cases of hacktivism and intellectual property theft are also occurring.
Facilitators and relevant factors
Many industries outsource parts of their business to third parties which may not match their security standards. Attackers will always target the weakest link and therefore corporate entities may be vulnerable via their third party suppliers.
The digital underground provides a variety of products and services which can facilitate network intrusion ranging from crimeware kits and customised malware to hacker-for-hire services. The proliferation of these services opens up the possibility to carry out attacks of this nature to any customers who otherwise lack the expertise or knowledge to initiate an attack unaided.
In March 2014, the European Parliament approved an amended version of the Network and Information Security (NIS) Directive. The directive originally included a requirement for a variety of Internet facing entities including e-commerce platforms, social networks and search engines to report to competent authorities any incident with impact on their core services - such as a data breach. However the amendment excluded these entities and limited the scope to companies providing critical infrastructure and supporting industries.







