Chapter 4 - Facilitators and relevant factors
4.1 Social networking - Overview
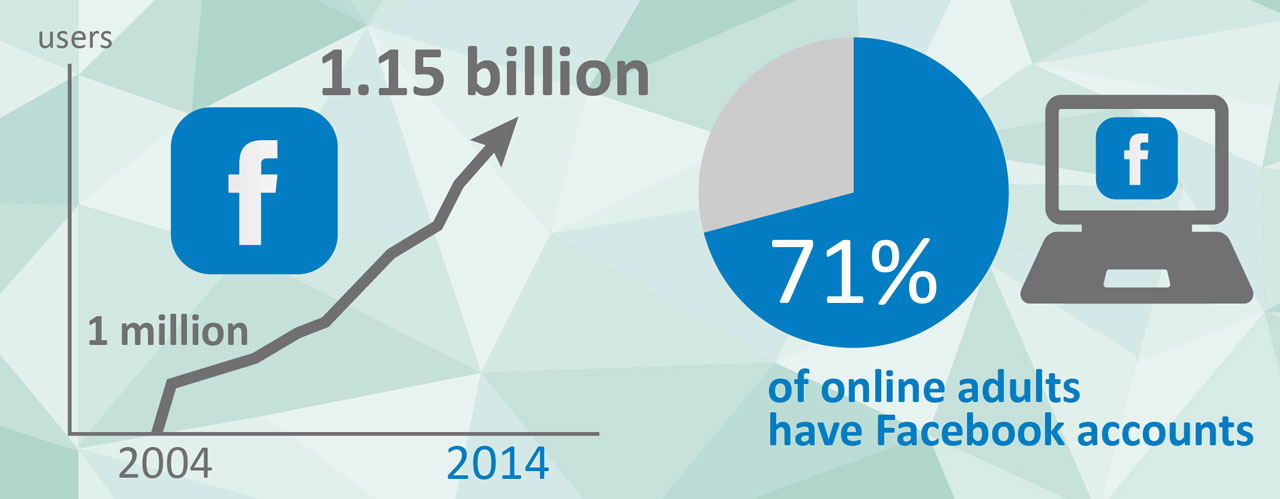
The proliferation of the Internet has brought about an unprecedented level of global social connectivity. The average Internet user spends 16 hours per month [147] online and 27% of that time is spent on social networking [148]. 2014 marks the 10 year anniversary of Facebook, the world’s largest social networking site. Following its success the last decade has seen an explosive growth in social media platforms. Facebook alone has grown in size from 1 million users in its first year to over 1.15 billion today; 71% of online adults have Facebook accounts [149]. Globally there are currently estimated to be almost 2 billion social network users, with over 310 million users within the EU [150].
Not only is the Internet becoming part of our daily lives, but our private and professional lives are increasingly becoming part of the open and accessible content of the Internet. Every Tweet, Like, Status Update, Tag, Pin, Comment, +Friend or Share increases our ever-expanding Internet footprint.
Attackers exploit the prolific sharing and posting of media on these websites. The combination of the viral nature of media sharing and the huge target audience makes social networking platforms a perfect resource for cyber criminals for the distribution and propagation of malicious content.
Criminal exploitation
Attacks via social media sites can take many forms. Despite the efforts of the providers, social networking sites are becoming an increasingly popular mechanism for distributing malware. Most attacks rely on victims clicking on malicious links or performing some other action which subsequently infects their device. These attacks typically also ’Like’ or ’Share’ the malicious content from the victim’s profile, resulting in the victims’ contacts further infecting themselves after viewing content they believed to be from a trusted source. In such a way the attacks propagate virally through the social media network [151]. Effectively, social networking sites are taking over from traditional spam.
Social media is also a perfect environment for attackers to employ social engineering tactics. By design, social platforms encourage users to share and disclose information. Attackers need only provide suitable incentives to potential victims for them to disclose private information or lure them to a malicious URL.

Social networking accounts also provide criminals with the materials they need for identity theft. Attackers can create accounts duplicating their victim, likely replicating media and data the victims have published themselves on their genuine accounts. These doppelganger accounts can then be used for further social engineering attacks on the victim’s contacts, exploiting their trusted relationships. Alternatively, compromised social networking accounts are a valuable commodity in the underground digital economy. In early 2012, the number of phishing sites targeting social networking sites briefly surpassed those targeting financial institutions [152]. Stolen and hacked accounts are a commonly reported problem for many law enforcement agencies. Consumer data is a valuable commodity. The mining of personal data by private companies is a growing trend in addition to its exploitation by criminals.
2013 saw data breaches in many of the major providers including Facebook, Twitter, LinkedIn, Last.fm, eHarmony and Living Social, collectively representing the compromise of almost 65 million users’ credentials.
Predictably, criminals also use social networking platforms to communicate with associates and recruit new members, although this is more common with criminals involved in more traditional crime.
Facilitators and relevant factors
The notion of privacy in cyberspace is somehow different to that in the off-line world. Users will disclose their private lives and personal details online without a comprehensive awareness of exactly who they are sharing their information with, whether it is the platform owner, a private company or the general public.
This leaves consumers extremely vulnerable to compromise from targeted attacks from social engineering and spear phishing and subsequently further fraud. This threat is exacerbated by the current trend in Single Sign On (SSO), whereby users can log into other services using their social media accounts. The compromise of a single account can therefore lead to the compromise of multiple linked accounts.







