Chapter 3 - Crime Areas
3.3 Child sexual exploitation online - Overview
Child sex offenders commit criminal offences with an element of sexual activity or sexual contact with a minor, thereby violating established legal and moral codes with respect to sexual behaviour.
Most child sex offenders are not part of any criminal network and usually operate alone, driven solely by their sexual interest in children.
However, this does not mean that offenders act in isolation from each other. They communicate among themselves within like-minded groups in cyberspace, using a variety of online tools, from IRC, ICQ, Yahoo newsgroups/forums to social networks, peer-to-peer file sharing networks, secure email and TOR. Even though it is commonly accepted that child sexual exploitation (CSE) offenders do not form typical organised crime groups, they still organize themselves in an analogous hierarchy on such platforms. This is usually the case on platforms where offenders exchange child abuse material (CAM), either in video, pictures or even text format. Here, those who provide material that is considered to be of ‘high quality’ (typically novel material), show higher levels of technical expertise and share best practise, can achieve the highest ranks and be recognised amongst their peers. Furthermore, some offenders affiliate themselves with each other in order to share physical access to children, therefore facilitating the production of new material, as well as its customisation.
The forensic awareness of CSE offenders can vary considerably, but evidence indicates that overall forensic skills are on the rise, which may be in response to improved detection and forensic policing. This increase in expertise is propagated in closed communities where it is common to find a section dedicated to technical and forensic guidance. The level of technical expertise is in some cases very advanced, indicating professional ICT and information security expertise.
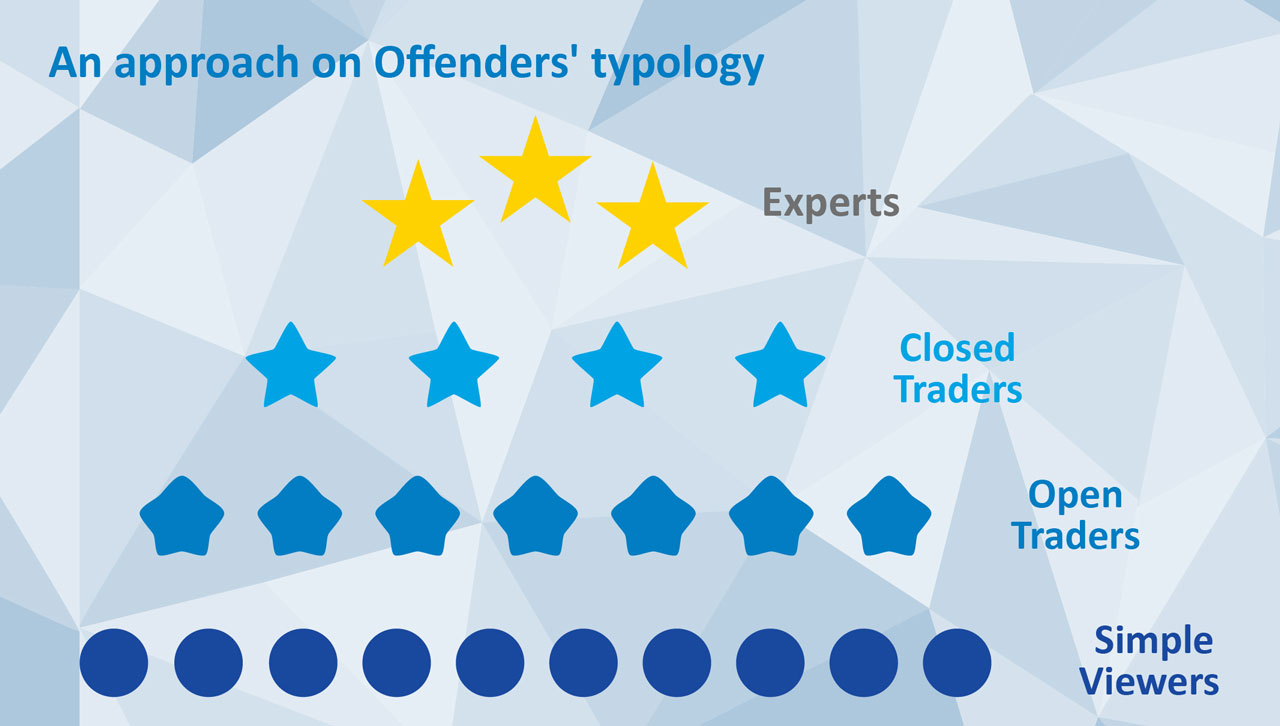
Aiken, M.; Moran, M. and Berry, M. (2011). Child abuse material and the Internet: Cyberpsychology of online child related sex offending

Exploitation of children online
Child sex offenders use the Internet to meet like-minded individuals, to have access to a wider pool of children, to share resources and knowledge and to disseminate CAM.
According to the threat assessment from the UK Child Exploitation and Online Protection Centre (CEOP), when taking into account the overall demographics of child sexual exploitation online (CSEO) - including sexual extortion and grooming - girls, of white ethnicity, aged between 11 and 14, are the main victims [43]. Nevertheless, information from the Internet Watch Foundation (IWF) reveals that when considering web pages containing child abuse material, a different demographic emerges: girls of white ethnicity are still the main victims but the age of the victims is considerably lower, with more than 80% of the victims younger than 10 [44]. Data from the International Association of Internet Hotlines (INHOPE) also shows an increase in infant victims of sexual abuse [45] and in abuse of an extreme and sadistic nature.

Sexual extortion and grooming
A major growing trend in CSE is sexual extortion, also known as sextortion, which, for the purpose of this document will be defined as coercion to extort sexual favours or images from a victim, usually by threatening to disseminate existing images of the victim if demands are not met. By exposing their personal details online without proper precautions, either via social media platforms or by sharing sexualised self-produced images, children and adolescents create the possibility of being targeted as potential victims by online predators.
An offender’s modus operandi typically involves initiating contact with youngsters on social media platforms. Offenders exploit the contact opportunities provided by social networking platforms and other types of computer mediated communication, creating groups of sometimes hundreds of online friends that they consider potential victims. With such a large pool of children to choose from, offenders can scan their profiles in search of vulnerabilities, while engaging in virtual interactions to see which ones are more prone to falling for their lures. Offenders usually focus on the children that respond favourably or remain engaged [46].
In one notable case, a child sex offender coerced children to engage in sexual acts in front of webcams. The offender would meet children on social media platforms and convice them to send him indecent images of themselves. Once the children complied with the request, the offender would coerce them to undertake more serious abuse with the threat of disseminating the pictures to the childrens’ friends and family if his demands were not met.
The offender used TOR and proxies to disguise his identity, but made a number of mistakes that led to his identification and arrest in the Netherlands.
The operation was led by the United Kingdom with the participation of EC3, US ICE, the Netherlands and Canada.
While most cases of sexual extortion seem to be initiated through an initial grooming process there is evidence of cases where the offenders have hacked into a victims’ personal computer or instigated them to download malicious software, compromising their computer and then scouring their social networks [47]. There are cases of offenders making use of images acquired in this manner to force the minors to engage in off-line contacts and proceed with physical abuse.
Many cases of sexual extortion are a consequence of ‘sexting’. Sexting can be defined as the ‘exchange of sexual messages or images’ [48], typically self-generated, sent via mobile phone or the Internet. This exchange frequently occurs between peers - young people consciously exchanging naked or sexualised images of themselves with one another. Technology can facilitate the further unwanted dissemination of the images, affecting the well-being of the originator, leading to harassment and bullying, online and off-line, self-harming or even suicide. The subject of self-generated images brings added challenges. In some jurisdictions it is sometimes considered that the minor who generated the picture and distributed it is guilty of producing and disseminating child abuse material [49].
It is worth highlighting that the scope of criminal activity is defined by the offender’s language skills. An offender speaking widely known languages is able to reach more potential targets, whereas an offender speaking a language which is not widespread will not extend beyond the national level.
Child sexual exploitation online on the Darknet
The use of the Darknet is increasingly popular among Europeans [50]. A large number of offenders, in particular the ones with greater security awareness and technical knowledge, have established communities using hidden services on platforms such as TOR. Within these hidden services there is a proliferation of social networking platforms and storage providers dedicated to child abuse material (CAM) where offenders can post and view CAM securely.
Platforms like TOR and the hidden services therein facilitate practically untraceable sexual exploitation of children by allowing the exchange of images anonymously through websites, private messages and email. They promote the request of on-demand abuse, allow offenders to anonymously create social network accounts to contact children and promote discussion among offenders on how to better groom and abuse children, where good destinations are for travelling child sex offenders (TCSOs) and how to obtain children there. These platforms encourage the normalisation of child abuse by the sharing of experience and justifications.
Having an awareness of many of the techniques employed by LE, offenders share guidance on how to sanitize material or mislead investigators, advising on removing EXIF [51] data from pictures and how to include misleading background details in the images. Best practices on how to rape, kidnap, murder and dispose of children’s bodies are also shared openly on Darknet forums [52] and the rape of children openly discussed [53]. CAM of a sadistic and violent nature is more readily available and there is also some evidence of a decrease in the age of the victims.
The existence of VIP or restricted sections is a common feature of most message boards, with access usually involving a vetting procedure frequently requiring production of new CAM, bringing added challenges to LE who, according to most jurisdictions, cannot usually provide this type of material within the law.
Services like ‘TOR chat’, designed to be untraceable, facilitate engagement among offenders. Recent developments on TOR include the possibility of downloading Apps onto mobile Android devices, as well as ‘safeplug’ hardware to anonymise web browsing by linking to wireless routers and streaming data onto TOR.
There are instances of CAM being exchanged via ‘TOR mail’ in exchange for Bitcoins. Even though most offenders do not exchange CAM for commercial reasons, the valuable significance of the material associated to the anonymity of TOR and Bitcoin creates the ideal setting to add a financial benefit to a traditional exchange.
Nevertheless some offenders on TOR claim that services with paid memberships do not fit into the TOR environment as it brings more insecurity to the process of sharing CAM online. According to CEOP’s research a good level of trust needs to be achieved in order to purchase CAM, with offenders arguing that if the material is not new it should be freely available while producers might charge for new material [54].

Overall there is a trend of child sex offenders moving into secure environments such as the Darknet, making use of its anonymity to facilitate the exchange of customised material, and therefore encouraging hands-on abuse.
Commercial sexual exploitation of children online (CSECO)
The traditional commercial exploitation of children online has seen a downward trend in recent years. The amount of commercially available CAM is estimated to be very low. The few investigators that were able to provide a percentage estimate mention an average of only 8.5% of commercial CAM.
In some cases of CSECO ‘hackers-for-hire’ are employed to hack servers of websites - typically those of small businesses hosted globally - in order to abuse their hosting. URLs directing individuals to commercial child abuse material hosted on the compromised server are distributed via spam. Typically these CSECO websites demand payment in Bitcoins [55]. However, most of these websites are fraudulent and only aimed at obtaining money from individuals seeking online CAM, without actually providing any material.
The once common use of credit cards for CSECO has seen a downward trend as a result of the proactive measures put in place by payment processors [56] and further availability of other, more anonymous, payment methods. Currently one of the upward trends for CSECO is the live streaming of abuse for which money transfer services seem to be the preferred payment method.
Live streaming of child abuse
The popularisation of webcams and chat platforms that enable the streaming of live images and video has led to their exploitation by child sexual abusers. Some applications allow users to upgrade their accounts by paying a fee, guaranteeing access to extended features such as broadcasts protected by passwords and extra layers of anonymity.
While live streaming is also common in sexual extortion cases, a trend has been detected concerning the abuse of children overseas, live in front of a camera at the request of Westerners. Payments per session can vary from USD 30 to USD 3000. A session allows the perpetrator the chance to orchestrate and view the abuse of a child in real time.
The abused children are from countries with deprived economies, typically in Eastern Asia. In the cases that have been investigated the financial profit is used to support the basic needs of the family or group involved. In these cases there has been a certain level of organisation, at a familial or community level.
The potential to earn money makes the crime of abuse via live streaming an attractive proposition. Payment for these services is made through international money transfer and, less frequently, via local money transfers.
The live streaming of child abuse is likely to be a growth area. It is a crime that is hard to detect and investigate since the offenders do not usually store a copy of the streamed material, therefore emphasis should be put on investigating the ordering and delivery of streamed CAM. In addition, the real-time monitoring of this type of transmission is legally and technically challenging.
The potential connection of live streaming to TCSOs should be taken seriously into consideration. The pay-per-view abuse of a child may lead to or be a consequence of the hands-on abuse of the same child. Those responsible for organising the online abuse may also be facilitating children’s physical abuse by offenders.
Facilitators and relevant factors
The most common method for offenders to exchange CAM is still Peer-to-Peer (P2P) platforms. This is facilitated by the ease of access to this type of platform and by the large amounts of CAM available for free within this medium. It is important to note that the offenders might start their online CSE criminal career by exchanging material in P2P, forums, emails, and other easily accessible platforms and move on to more sophisticated methods of accessing and distributing CAM, such as the Darknet.
The Darknet represents a significant threat in this area. The anonymity granted by these platforms is a strong enabling factor.
The use of encryption is also increasing and includes measures such as compressed files through to full disk and server encryption. Until recently Truecrypt was the most commonly used tool for encryption, together with BitLocker for full disk encryption. For server encryption Luks is frequently used.
Many offenders take their security very seriously, investing not only in encryption but taking other defensive measures such as using VPNs (Virtual Private Networks), secure email, disposable emails, proxies, prepaid Internet access, bullet-proof hosting services [57], free WiFi connections and disk wiping tools.
The usage of cloud services within CSEO is not yet common but is an emerging trend. These services allow offenders to store CAM remotely, enabling removal of materials from a distance.
Another facilitating factor for this crime is the increase in mobile devices and apps, which enable constant connection to the online world by both potential victims and offenders.







